Find all valuable assets
across the organization that could be harmed by threats in a way that results in a monetary loss. Here are just a few examples:
• Servers
• Website
• Client contact information
• Partner documents
across the organization that could be harmed by threats in a way that results in a monetary loss. Here are just a few examples:
• Servers
• Website
• Client contact information
• Partner documents
Determine what financial losses the organization would suffer if a given asset were damaged. Here are some of the consequences you should care about:
• Data loss
• System or application downtime
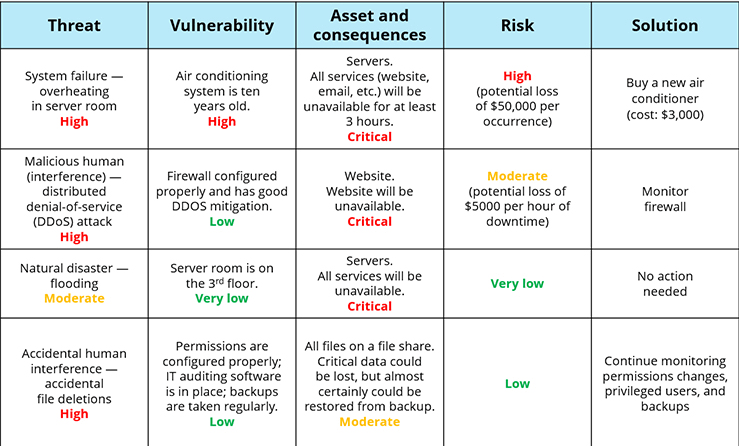
threat is anything that might exploit a vulnerability to breach your security and cause harm to your assets. Here are some common threats:
• Natural disasters
• System failure
• Accidental human interference
• Malicious human actions (interference, interception or impersonation)
of their exploitation. A vulnerability is a weakness that allows some threat to breach your security and cause harm to an asset. Think about what protects your systems from a given threat — if the threat actually occurs, what are the chances that it will actually damage your assets? Vulnerabilities can be physical (such as old equipment), problems with software design or configuration (such as excessive access permissions or unpatched workstations), or human factors (such as untrained or careless staff members).
Risk is the potential that a given threat will exploit the vulnerabilities of the environment and cause harm to one or more assets, leading to monetary loss. Assess the risk according to the logical formula stated above and assign it a value of high, moderate or low. Then develop a solution for every high and moderate risk, along with an estimate of its cost.
(server failure) → Response (use your disaster recovery plan or the vendor’s documentation to get the server up and running) → Analysis (determine why this server failed) → Mitigation (if the server failed due to overheating because of low-quality equipment, ask your management to buy better equipment; if they refuse, put additional monitoring in place so you can shut down the server in a controlled way)